
by Douglas Stinson
CRC Press, CRC Press LLC
ISBN: 0849385210 Pub Date: 03/17/95

|
Cryptography: Theory and Practice
by Douglas Stinson CRC Press, CRC Press LLC ISBN: 0849385210 Pub Date: 03/17/95 |
| Previous | Table of Contents | Next |

The probability distributions on 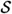 and
and 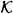 are as follows:
are as follows:

What are the optimal impersonation and substitution strategies?

of C. Prove that C is indeed an OA(n1 n2, k, λ1 λ2).

Compare the entropy bounds for Pd0 and Pd1 with the actual values you computed in Exercise 10.1.
HINT To compute 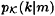 , use Bayes’ formula
, use Bayes’ formula

We already know how to calculate 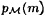 . To compute
. To compute 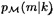 , write m = (s, a) and then observe that
, write m = (s, a) and then observe that 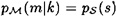 if ek(s) = a, and
if ek(s) = a, and 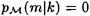 otherwise.
otherwise.
To compute 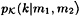 , use Bayes’ formula
, use Bayes’ formula

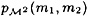 can be calculated as follows: write m1 = (s1, a1) and m2 = (s2, a2). Then
can be calculated as follows: write m1 = (s1, a1) and m2 = (s2, a2). Then
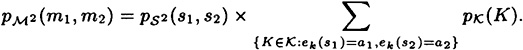
(Note the similarity with the computation of p(m).) To compute 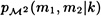 , observe that
, observe that 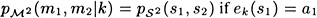 and ek(s2) = a2, and
and ek(s2) = a2, and 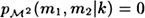 , otherwise.
, otherwise.
| Previous | Table of Contents | Next |